Table of contents
Broken Access Control is the number one vulnerability on the OWASP top 10 list, and I understand why, almost every pentest I conduct I find an access control issue, some of them are low impact and some of them are higher impact.
In this post, I am going to share one that had a higher impact and was easy to find. Not all access control vulnerabilities are as straightforward as this one but this post highlights that in some cases this can be very impactful without too much effort.
How I did do it?
I had two registered accounts one for a low-privileged user and one for an admin account.
Logged in to both accounts and I was looking for differences in the two accounts and functionalities specific to the admin account.
With Autorize turned on in Burp, I was browsing the admin account with the low-privileged user cookies and noticed that some endpoints have the same content length indicating that I have some sort of access control issue.
Made a note of those endpoints, and I simply copied them to the normal user account and sure enough this was granting access to a functionality where I could change the level of user access.
I could have done the same without using Autorize but what I want to show here is the methodology used to test for access control vulnerabilities.
For obvious reasons, the screenshot is redacted but what essentially is happening is that the endpoint highlighted was an endpoint that was specific to the admin account and copied over to the low-privileged user account and this granted access to the functionality where I was able to grant admin privileges not only to myself but to any other registered user.
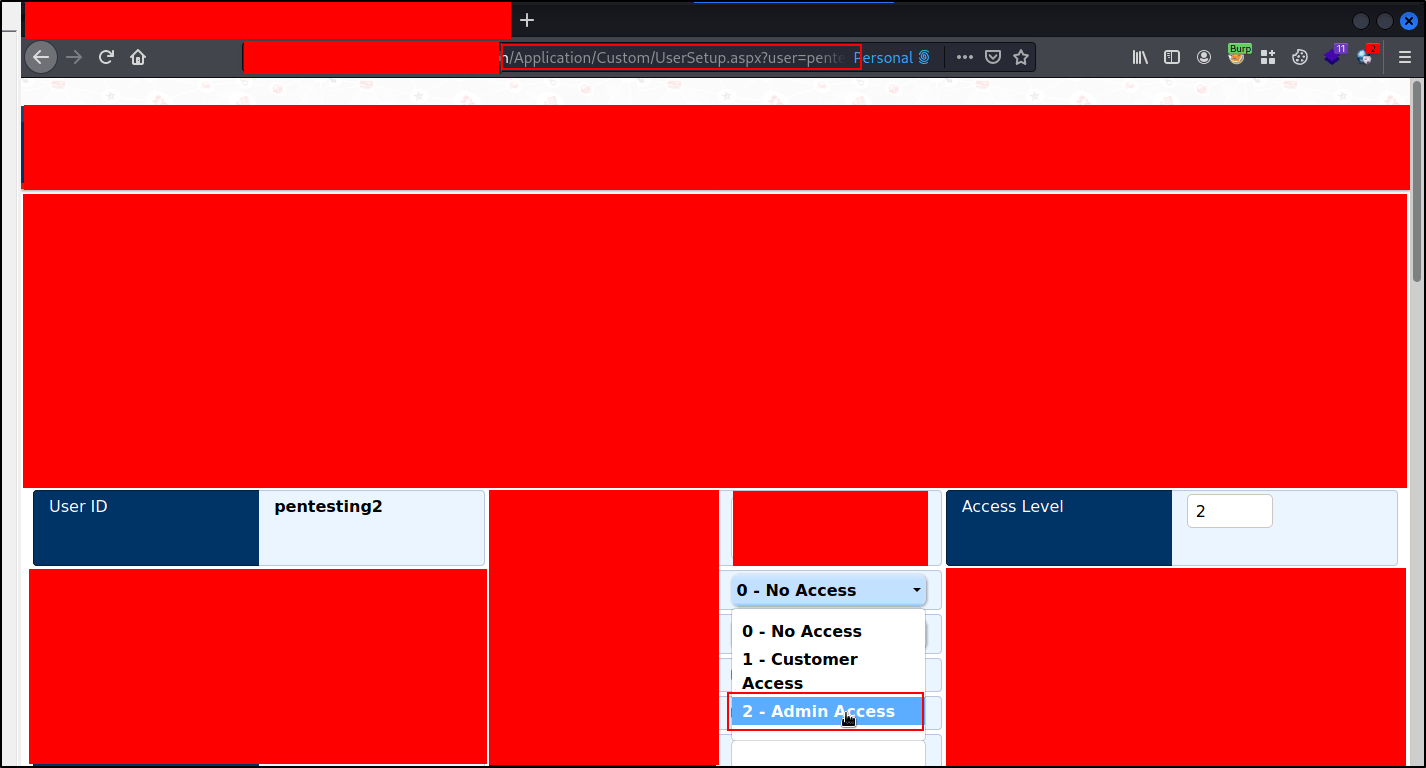
Steps
Logged in to both the normal user and the admin accounts and looked for differences in the accounts
Used Autorize to browse the admin account functionalities with the low-privileged user cookies
Looked for the content length and analysed the responses
Made note of the endpoints where the response was the same length
Copied the endpoints specific to the admin account into the normal user's account
Changed the user's privilege to admin
Hope you enjoyed this short demonstration. Stay curious and see you next time.
